In today’s digital age, cybersecurity threats are more prevalent than ever. Organizations of all sizes, from small businesses to large enterprises, are at risk of cyberattacks that can lead to data breaches, financial loss, and reputational damage. To mitigate these risks, it’s crucial to implement robust security measures. One effective approach is to adopt the CIS Controls.
What are the CIS Controls?
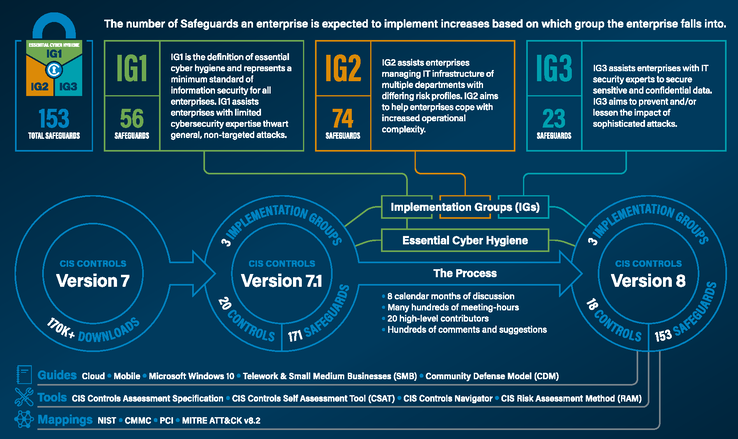
The CIS Controls are a set of cybersecurity best practices developed by the Center for Internet Security (CIS). These controls are designed to help organizations of all sizes improve their cybersecurity posture by focusing on the most critical areas of security. The CIS Controls are regularly updated to address emerging threats and technologies.
Key Benefits of Implementing CIS Controls
- Enhanced Security Posture: By following the CIS Controls, organizations can significantly strengthen their security defenses against a wide range of cyber threats.
- Reduced Risk of Breaches: Implementing these controls helps to minimize the likelihood of successful cyberattacks, which can lead to significant financial and reputational damage.
- Improved Compliance: Many regulatory frameworks, such as HIPAA and PCI DSS, align with the CIS Controls. By adhering to these controls, organizations can demonstrate compliance with industry standards.
- Cost-Effective Security: The CIS Controls provide a practical and cost-effective approach to cybersecurity. They prioritize the most critical security measures, allowing organizations to allocate resources efficiently.
- Proactive Security: The CIS Controls encourage a proactive approach to security, enabling organizations to identify and address potential vulnerabilities before they can be exploited by attackers.
How to Implement CIS Controls
Implementing the CIS Controls involves a multi-step process:
- Assess Your Organization’s Risk Profile: Identify the specific threats and vulnerabilities that your organization faces.
- Prioritize Controls: Focus on the controls that will have the greatest impact on your organization’s security posture.
- Develop an Implementation Plan: Create a detailed plan outlining the steps needed to implement each control.
- Implement Controls: Deploy the necessary technologies and processes to enforce the controls.
- Monitor and Evaluate: Continuously monitor your security posture and evaluate the effectiveness of the implemented controls.
By following these steps and leveraging the CIS Controls, organizations can significantly enhance their cybersecurity resilience and protect their valuable assets.
Conclusion
In today’s threat landscape, cybersecurity is no longer an option; it’s a necessity. The CIS Controls provide a proven framework for improving security and reducing risk. By investing in cybersecurity and adopting the CIS Controls, organizations can safeguard their future and build a more secure digital world.