WSL is a feature in Windows that allows you to run Linux environments directly on your Windows system. This means you can use Linux tools, commands, and utilities without the need for a virtual machine or dual-booting. It provides a seamless integration between Windows and Linux, making it a popular choice for developers, system administrators, and anyone who wants to leverage the power of Linux on their Windows machine including hackers who can now install Kali linux and utilize every possible tool directly from the within.
How to Install WSL:
Installation is simple by using PowerShell:
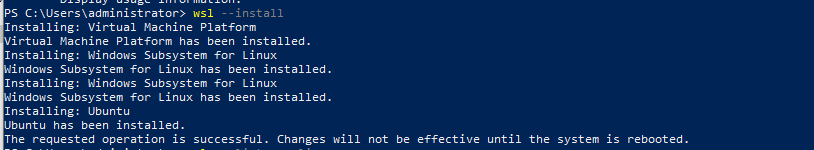
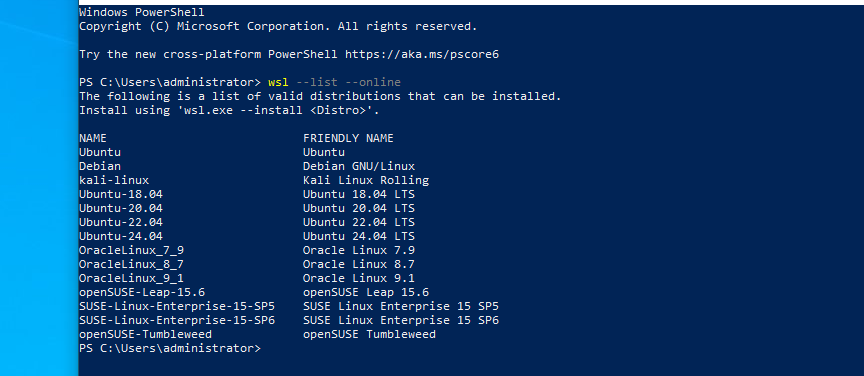
You can even chose which distribution you would like to have deployed by utilizing command wsl --install -d <Distribution Name> Shout Out Kali Linux is available.
Potential Attack Vectors in WSL:
While WSL offers many benefits, it also introduces new potential attack vectors:
- Misconfigurations:
- Weak passwords: Using weak or default passwords for Linux user accounts can make them vulnerable to brute-force attacks.
- Insecure permissions: Incorrect file and directory permissions can expose sensitive information.
- Outdated software: Running outdated Linux distributions or software can leave you exposed to known vulnerabilities.
- Exploiting Linux Vulnerabilities:
- Kernel vulnerabilities: Exploiting kernel vulnerabilities can lead to system compromise.
- Application vulnerabilities: Attackers can exploit vulnerabilities in Linux applications to gain unauthorized access.
- Leveraging WSL as an Attack Platform:
- Persistence mechanisms: Attackers can use WSL to establish persistence on a compromised system.
- Lateral movement: WSL can be used to pivot to other systems within a network.
- Data exfiltration: Attackers can use WSL to exfiltrate sensitive data.
Mitigating Risks:
- Keep WSL and Linux distributions up-to-date: Regularly update your Linux distributions and installed packages to address security vulnerabilities.
- Use strong, unique passwords: Create strong, complex passwords for your Linux user accounts.
- Configure secure permissions: Set appropriate file and directory permissions to protect sensitive information.
- Enable security features: Use tools like
fail2banto block brute-force attacks andufwto configure a firewall. - Monitor WSL activity: Use security monitoring tools to detect unusual activity within your WSL environment.
- Segment WSL from the host system: Avoid running critical services or storing sensitive data within WSL.
- Educate users: Train users on best practices for using WSL securely.
- Block the feature: best choice is to not have an option to install it at all.
By following these guidelines, you can mitigate the risks associated with WSL and ensure the security of your Windows system.

