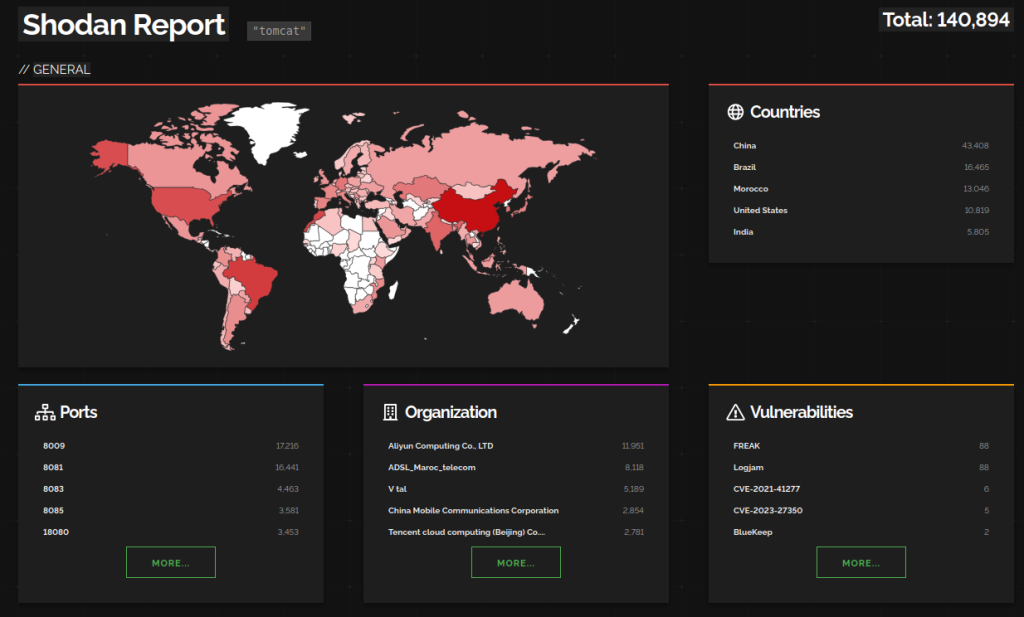
Apache Tomcat is a versatile and widely-used platform for developing and deploying Java-based web applications. Its open-source nature, stability, and ease of use make it a popular choice among developers and organizations worldwide. Any major vulnerability on this platform is critical as it is being used by more then 140 000 instances reachable online.
A new vulnerability identified by Nacl, WHOAMI, Yemoli and Ruozhi. has been reported and there is also a PoC script out.
The vulnerability, tracked as CVE-2024-56337, has been described as an incomplete mitigation for CVE-2024-50379 (CVSS score: 9.8), another critical security flaw in the same product that was previously addressed on December 17, 2024.
Users running Tomcat on a case insensitive file system with the default servlet write enabled (readonly initialisation parameter set to the non-default value of false) may need additional configuration to fully mitigate CVE-2024-50379 depending on which version of Java they are using with Tomcat.
Mitigation:
Users of the affected versions should apply one of the following
mitigations:
- Upgrade to Apache Tomcat 11.0.2 or later
- Upgrade to Apache Tomcat 10.1.34 or later
- Upgrade to Apache Tomcat 9.0.98 or later
- running on Java 8 or Java 11: the system property
sun.io.useCanonCaches must be explicitly set to false (it defaults
to true) - running on Java 17: the system property sun.io.useCanonCaches,
if set, must be set to false (it defaults to false) - running on Java 21 onwards: no further configuration is required
(the system property and the problematic cache have been removed)
Considering that the PoC is out, this should be a priority for remediation.