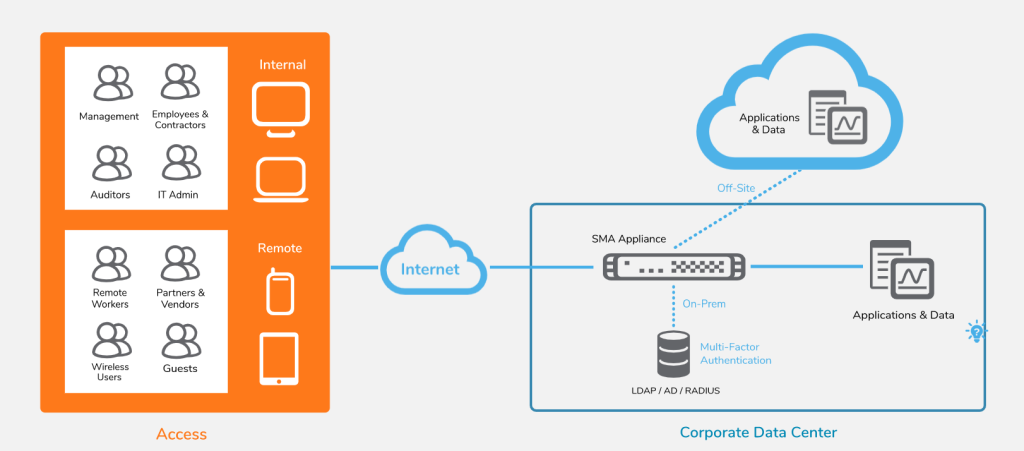
SonicWall SMA 100 is a secure remote access solution designed for small and medium businesses (SMBs) with 50-100 employees. It allows authorized users to securely access corporate resources from anywhere, using any device, while ensuring that only trusted users and devices are granted access. The solution can be deployed on-prem, in cloud and also as a virtual appliance. The clients can use web interface, SonicWall moblie client or 3rd party VPN client for access and authorization.
Now that we covered basics, it was reported by Alain Mowat of Orange Cyberdefense, Switzerland that the solution has multiple vulnerabilities described below with highest CVSS score being at 8.1.
1) Path traversal vulnerability – attributed to publicly known Apache HTTP Server vulnerability (CVE-2024-38475)
Improper escaping of output in mod_rewrite in Apache HTTP Server 2.4.59 and earlier allows an attacker to map URLs to file system locations that are permitted to be served by the server.
CVSS Score: 7.5
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
CWE-35: Path traversal vulnerability
2) CVE-2024-40763 – SonicWALL SMA100 Heap-based buffer overflow vulnerability
Heap-based buffer overflow vulnerability in the SonicWall SMA100 SSLVPN due to the use of strcpy. This allows remote authenticated attackers to cause Heap-based buffer overflow and potentially lead to code execution.
CVSS Score: 7.5
CVSS Vector: CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE-122: Heap-based Buffer Overflow
3) CVE-2024-45318 – Stack-based buffer overflow vulnerability
A vulnerability in the SonicWall SMA100 SSLVPN web management interface allows remote attackers to cause Stack-based buffer overflow and potentially lead to code execution.
CVSS Score: 8.1
CVSS Vector: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
CWE-121: Stack-based Buffer Overflow
4) CVE-2024-45319 – Certificate-based authentication bypass
A vulnerability in the SonicWall SMA100 SSLVPN allows a remote authenticated attacker can circumvent the certificate requirement during authentication.
CVSS Score: 6.3
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L
CWE-798: Use of Hard-coded Credentials
5) CVE-2024-53702 – Insecure randomness
Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG) in the SonicWall SMA100 SSLVPN backup code generator that, in certain cases, can be predicted by an attacker, potentially exposing the generated secret.
CVSS Score: 5.3
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
CWE-338: Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG)
6) CVE-2024-53703 – Stack-based buffer overflow vulnerability
A vulnerability in the SonicWall SMA100 SSLVPN mod_httprp library loaded by the Apache web server allows remote attackers to cause Stack-based buffer overflow and potentially lead to code execution.
CVSS Score: 8.1
CVSS Vector: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
CWE-121: Stack-based Buffer Overflow
There is no evidence that these vulnerabilities are being exploited in the wild and SonicWall SSL VPN SMA1000 series products are not affected by these vulnerabilities.