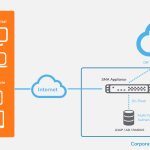
The CISA, in collaboration with international and U.S. partners like the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), has published guidance for organizations looking to implement Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms. This article focuses on the implementation of Security Information and Event Management (SIEM) […]
Category: Information Security
The importance of naming services online is that it helps users find and understand what the service does. A well-chosen name can also help to build trust and credibility with potential users. When we look back and see some of the changes in naming conventions for popular services, its hard to understand the logic of […]
FIDO2 is an open authentication standard that enables users to log in to online services without using a password. It uses public key cryptography to provide strong authentication that is resistant to phishing and other online attacks. To use FIDO2, you will need a compatible device and an account with a service that supports FIDO2 […]
Microsoft’s aggressive push into AI, particularly with its integration into Microsoft 365, has the potential to significantly impact how companies approach data security. Let’s consider data for company through CIA triad, AI is currently overstepping all three of the pillars by it’s integration. How can data be confident if AI has access without any restriction, […]
Steganography is a technique used to hide data within another file or message, making it difficult to detect. It’s different from encryption, which scrambles data to make it unreadable without a key. Instead, steganography conceals the existence of the hidden data itself. How Steganography Works: There are various methods of steganography, but they all involve […]
The researchers from 0Patch have discovered a vulnerability on all Windows Workstation and Server versions from Windows 7 and Server 2008 R2 to the latest Windows 11 v24H2 and Server 2022. The vulnerability allows an attacker to obtain user’s NTLM credentials by simply having the user view a malicious file in Windows Explorer. This vulnerability […]
Neuromarketing and persuasive communication are two fields that have become increasingly intertwined in recent years. By understanding how the brain processes information and makes decisions, marketers can create more effective messages that resonate with their target audience. While these were all known and studied for years and years, we need to take into consideration additional […]
SonicWall SMA 100 is a secure remote access solution designed for small and medium businesses (SMBs) with 50-100 employees. It allows authorized users to securely access corporate resources from anywhere, using any device, while ensuring that only trusted users and devices are granted access. The solution can be deployed on-prem, in cloud and also as […]
An attack surface is the sum total of all the potential points of entry that an attacker can exploit to gain unauthorized access to a system, network, or organization. These points of entry can be physical or digital, and they can include vulnerabilities in software, hardware, networks, or human processes. Infrastructure documentation is crucial for […]
Technical debt or tech debt is a metaphor used to describe the consequence of choosing a quick and easy solution over a more robust, long-term solution. This debt accumulates over time and can lead to increased maintenance costs, reduced development velocity, and increased risk of system failures. Examples of Tech Debt in IT Software to […]