The CIS Critical Security Controls Navigator is a free interactive tool that provides detailed mapping information for both CIS Controls version 7.1 and version 8. This tool makes it easy for organizations to explore how the CIS Controls align with various standards and frameworks. How to use it: Features and Benefits: Additional Resources: Conclusion: The […]
Sender Policy Framework (SPF) is a critical email authentication protocol that helps prevent email spoofing. However, misconfigurations in SPF records can lead to several issues, impacting email deliverability and security. The ~all Qualifier The ~all qualifier in an SPF record is a critical element that determines how receiving mail servers should handle emails that don’t […]
OWASP ZAP (Zed Attack Proxy) is a robust open-source web application security scanning tool that helps identify and mitigate vulnerabilities. Its user-friendly interface and extensive feature set make it a popular choice for both security professionals and developers. Key Features of OWASP ZAP: Why OWASP ZAP is a Great Tool: Comparison to Other Tools: While […]
Windows 11 24H2, Microsoft’s latest major update for its operating system, has been plagued with a series of issues since its release. While the update aims to enhance performance and security, it has unfortunately introduced several problems that are causing headaches for many users. Here’s a breakdown of the most prominent issues reported so far: […]
The MITRE ATT&CK framework has become an indispensable tool for both defenders and attackers in the cybersecurity landscape. This comprehensive knowledge base, developed by the MITRE Corporation, provides a standardized taxonomy of adversary tactics, techniques, and procedures (TTPs). By understanding how attackers operate, organizations can enhance their security posture and proactively defend against threats. Why […]
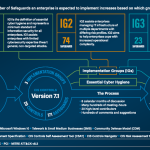
In today’s digital age, cybersecurity threats are more prevalent than ever. Organizations of all sizes, from small businesses to large enterprises, are at risk of cyberattacks that can lead to data breaches, financial loss, and reputational damage. To mitigate these risks, it’s crucial to implement robust security measures. One effective approach is to adopt the […]