Steganography is a technique used to hide data within another file or message, making it difficult to detect. It’s different from encryption, which scrambles data to make it unreadable without a key. Instead, steganography conceals the existence of the hidden data itself.
How Steganography Works:
There are various methods of steganography, but they all involve modifying an existing file (like an image, audio file, or text document) to hide the secret information within it. Some common techniques include:
- Least Significant Bit (LSB) Steganography: This involves modifying the least significant bits of the file’s pixels or bytes. Since these bits have the least impact on the file’s appearance or sound, the changes are often imperceptible.
- Covering Codes: These are techniques that allow information to be embedded in the redundancy of the cover file, such as the unused parts of a compressed image.
- Spread Spectrum: This involves spreading the hidden data across the entire cover file, making it difficult to detect by statistical analysis.
Steganography in Cybersecurity:
Example of usage for hiding text:
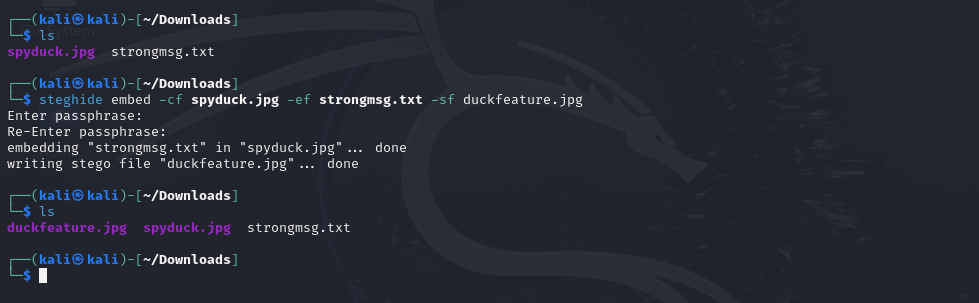
The hidden message is stored in the file strongmsg.txt and hidden with the image spyduck.jpg. The feature image of this post is that duckfeature.jpg so, feel free to test your skills by utilizing steghide and the passphrase is : cool
Steganography can be used for both legitimate and malicious purposes in cybersecurity:
Legitimate Uses:
- Data Hiding: Protecting sensitive information by hiding it within seemingly innocuous files.
- Covert Communication: Establishing secret communication channels.
- Digital Watermarking: Embedding copyright information or ownership claims into digital media.
Malicious Uses:
- Data Exfiltration: Stealing sensitive data and hiding it within other files to avoid detection.
- Malware Distribution: Hiding malicious code within seemingly harmless files.
- Command and Control: Establishing covert communication channels for controlling botnets or other malicious activities.
Detecting Steganography:
Detecting steganography can be challenging, as it often relies on statistical analysis and pattern recognition. Some techniques used to detect steganography include:
- Statistical Analysis: Identifying statistical anomalies in the cover file that might indicate hidden data.
- Pattern Recognition: Looking for patterns in the data that suggest the presence of a hidden message.
- Specialized Steganalysis Tools: Using software designed to detect steganography.
While steganography can be a powerful tool for both protection and malicious activities, it’s important to be aware of its potential uses and the techniques for detecting it

