The researchers from 0Patch have discovered a vulnerability on all Windows Workstation and Server versions from Windows 7 and Server 2008 R2 to the latest Windows 11 v24H2 and Server 2022. The vulnerability allows an attacker to obtain user’s NTLM credentials by simply having the user view a malicious file in Windows Explorer.
This vulnerability still does not have a CVE id and technical details are not disclosed but, from previous vulnerabilities and how the technology works around NTLM, we can conclude that clicking or opening the file, logged in NTLM hash is being shared with third party.
NTLM (NT LAN Manager) is a suite of Microsoft authentication protocols used to provide authentication, integrity, and confidentiality to users in a network environment. It’s primarily used for authenticating client-server interactions within a Windows domain. Nowadays Kerberos is a primary authentication protocol but most system have NTLM as a backup in case it is needed for older applications or Kerberos fails/is not available at a time.
Example of NTLM hash cracked on crackstation online
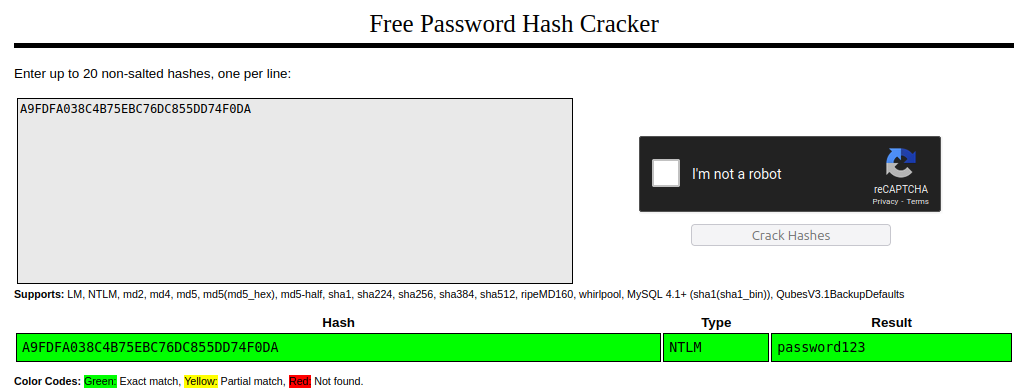
By getting logged in user hash value, malicious actor can try to crack it with tools such as Hashcat, Crackstation, Jack the Ripper. Now, important thing with this is that proper password policy can mitigate the impact as having, for example, 14 character password with password complexity enforced will take years to crack..
Users may consider turning off NTLM authentication with a Group Policy on ‘Security Settings > Local Policies > Security Options’, and configuring the “Network security: Restrict NTLM” policies. This should be something your administrator in company need to review and assess impact if needed.
Source: https://blog.0patch.com/2024/12/url-file-ntlm-hash-disclosure.html