Neuromarketing and persuasive communication are two fields that have become increasingly intertwined in recent years. By understanding how the brain processes information and makes decisions, marketers can create more effective messages that resonate with their target audience. While these were all known and studied for years and years, we need to take into consideration additional […]
Author: Josip
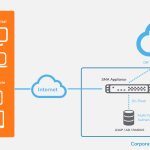
SonicWall SMA 100 is a secure remote access solution designed for small and medium businesses (SMBs) with 50-100 employees. It allows authorized users to securely access corporate resources from anywhere, using any device, while ensuring that only trusted users and devices are granted access. The solution can be deployed on-prem, in cloud and also as […]
PNETLab is a free, open-source platform that enables you to create and manage complex network simulations. It offers a user-friendly interface and a vast library of network devices, making it an excellent tool for network engineers, students, and enthusiasts to learn, practice, and experiment with network technologies. As a cybersecurity professional, we often need to […]
An attack surface is the sum total of all the potential points of entry that an attacker can exploit to gain unauthorized access to a system, network, or organization. These points of entry can be physical or digital, and they can include vulnerabilities in software, hardware, networks, or human processes. Infrastructure documentation is crucial for […]
Hydra, also known as THC-Hydra, is a powerful and versatile tool used for penetration testing and security assessment. It specializes in brute-force attacks, a technique that involves systematically trying different combinations of usernames and passwords until the correct one is found. This makes it a valuable tool for identifying weaknesses in systems and networks. Key […]
Technical debt or tech debt is a metaphor used to describe the consequence of choosing a quick and easy solution over a more robust, long-term solution. This debt accumulates over time and can lead to increased maintenance costs, reduced development velocity, and increased risk of system failures. Examples of Tech Debt in IT Software to […]
It’s not a Christmas Miracle
Cybersecurity threats are a growing concern, and the holiday season is no exception In fact, cybercriminals often take advantage of the increased online activity and relaxed security measures during this time to launch their attacks. You might remember some of events such as “Leaksmas” when in the days leading up to Christmas, cybercriminals leaked […]
Artificial Intelligence (AI) and Blockchain are two of the most transformative technologies of our time, each with the potential to revolutionize industries and reshape society. When combined with the power of Large Language Models (LLMs), they create a potent synergy that is both exciting and concerning. Some of most notable solutions and frameworks are: TensorFlow, […]
The cybersecurity landscape is constantly evolving. For the most accurate and up-to-date information on supply chain vulnerabilities and their associated CVE details, please refer to reputable sources like the National Vulnerability Database (NVD) or consult with a cybersecurity expert. Disclaimer: The following information is based on known vulnerabilities in 2024 and might not be exhaustive. […]
WSL is a feature in Windows that allows you to run Linux environments directly on your Windows system. This means you can use Linux tools, commands, and utilities without the need for a virtual machine or dual-booting. It provides a seamless integration between Windows and Linux, making it a popular choice for developers, system administrators, […]